uni-notes
:mortar_board: Sunway University BSc in CS notes :memo: (201701 intake)
NET3204 Distributed Systems
- NET3204 Distributed Systems
Chapter Notes
Characterization of DS
What is a distributed system?
“A system in which hardware or software components located at networked computers communicate and coordinate their actions only by message passing. - Coulouris
“A distributed system is a collection of independent computers that appear to the users of the system as a single computer.” - Tanenbaum
“A distributed system is one on which I cannot get any work done because some machine I have never heard of has crashed.” - Leslie Lamport
Why Distributed Systems?
| Reason | Examples |
|---|---|
| Functional separation | Clients and Servers, and data collection and processing |
| Inherent distribution | Information, people, inventory systems, etc |
| Power imbalance & load variation | Distribute load |
| Reliability | data replication at different locations |
| Economics | sharing reduces cost, building using common off-the-shelf components is cheaper |
Consequences, Characteristics, Goals, Trends, Challenges
- Consequences
- Concurrency
- Heterogeneity
- No global clock
- Independent failures
- Goals
- Connecting Users and Resources
- Transparency
- Openness
- Scalability
- Enhanced Availability
- Trends
- Pervasive networking & modern Internet
- Mobile and ubiquitous computing
- Distributed multimedia systems
- Distributed computing as a utility
| Characteristics | Explanation |
|---|---|
| Parallel activities | |
| Communication via message passing | No shared memory |
| Resource sharing | |
| No global state | No single process knows the global state |
| No global clock | Limited precision for processes to sync their clocks compared to non-DS |
| Challenges | Means |
|---|---|
| Heterogeneity | components must be able to interoperate across different OSes, hardware arch, comm arch, languages, software interfaces, security measures & information rep |
| Openness & Interoperability | to have interfaces be publicly available to ease inclusion of new components (open specifications, standards from ANSI, ISO, IEEE, etc) |
| Security | distributed system used as intended (confidentiality, integrity, availability, non-repudiation, encryption, authentication, authorization) |
| Scalability | efficient operation even with increasing users by adding resources (challenges: cost, performance loss, bottlenecks) |
| Fault Tolerance | failure of 1 component != system-wide failure (fault detection, masking, toleration, recovery) |
| Concurrency | requires shared access to resources (fair scheduling, preserve dependencies, avoid deadlocks) |
| Distribution Transparency | should be hidden from the user as much as possible (access, location, failure, replication, migration, concurrency, performance, scaling, persistence, transactional transparency) |
| Quality of Service | The quality of the distributed system through reliability, security, performance, adaptability |
System Models
Physical Models
- captures the hardware composition of a system in terms of computer hardware and interconnecting networks.
- model represents underlying hardware elements
- abstracts away from specific details of the computer and networking technologies employed.
- is the baseline physical model - how hardware or software components located at networked computers communicate and coordinate their action by only passing messages.
- has 3 generations of distributed systems
- Early distributed systems (1970s to early 1980s)
- Internet-scale distributed systems
- Contemporary distributed systems
| Distributed Systems | Early | Internet-scale | Contemporary |
|---|---|---|---|
| Scale | Small | Large | Ultra-large |
| Heterogeneity | Limited (typically relatively homogenous configurations) | Significant in terms of platforms, languages, and middleware | Added dimensions introduced including radically different styles of architecture. |
| Openness | Not a priority | Significant priority with range of standards introduced | Major research challenge with existing standards not yet able to embrace complex systems. |
| Quality of Service | In its infancy | Significant priority with range of services introduced | Major research challenge with existing services not yet able to embrace complex systems. |
Architectural Models
- discusses in terms of computational and communication tasks perform by its computational elements that are supported by appropriate network interconnections.
- its structure in terms of separately specified components and their interrelationships
- major concerns are to make the system reliable, manageable, adaptable, cost effective
- three approaches:
- looking at core underlying architectural elements that underpin modern Distributed Systems,
- examining composite architectural patterns that are used in isolation or in combination with developing more sophisticated Distributed Systems, and
- considering middleware platforms to support the various styles of programming.
- plenty of trade-offs associated with the choices identified in terms of architectural elements employed
Communication Entities
From system perspective:
- Processes are typically the communicating elements coupled with appropriate inter-process communication paradigms.
- simpler environments such as sensor networks uses the term nodes in which OS processes are not supported.
- most distributed environments have processes supplemented by threads, hence entities communicating in such systems are called nodes
From programming perspective, more problem-oriented abstraction have been proposed:
- Objects - OOP approaches in Distributed Systems
- Components - use emerged due to weaknesses in objects. Components resemble objects, key difference being components specify not only their interfaces but also assumes other components/interfaces are present for a component to fulfill its function
- Web Services - closely related to objects and components, it is integrated into the World Wide Web, using web standards. It can be viewed as complete services in their own right.
Communication Paradigms
Entities communicate in Distributed Systems via:
- Inter-process Communication - low-level support: message passing primitives, communication between processes, API to IP socket programming, multicast communication
- Remote Invocation - based on 2-way exchange between communicating entities, with results from calling remote operations, procedures, or methods. (Request-reply protocol, RPC, RMI)
- Indirect Communication - group communication, publish-subscribe system, message queues, tuple spaces, distributed shared memory.
| Communicating Entities | Communication Paradigms |
|---|---|
| System-oriented Entities | Inter-process Communication |
| - Nodes, Processes | - Message Passing, Sockets, Multicast |
| Problem-oriented Entities | Remote Invocation |
| - Objects, Components, Web Services | - Request-reply, RPC, RMI |
| Indirect Communication | |
| - Group Communication, Pub-sub, DSM | |
| - Message Queues, Tuple spaces |
Roles and Responsibilities
In a Distributed System, processes take on given roles and these roles are fundamental in establishing the overall architecture to be adopted.
Two architectural styles stemming from the role of individual processes:
- Client-Server
- client processes interact with individual server processes in usually separate host computers to access shared resources. (Eg, HTTP, FTP)
- Peer-to-peer
- all processes involved in a task or activity play similar roles, interacting cooperatively as peers without any distinction between client-server processes
Architecture Pattern
- is a pattern to build on more primitive architectural elements
- not necessarily complete on its on but offers partial insights, when combined with other patterns, helps the designer find a solution
- Key architectural patterns in Distributed Systems:
- Layering
- Tiered architecture
- Thin clients
- Middleware
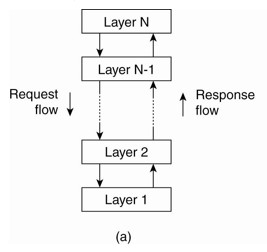
Layering
- this approach partitions a complex system into a number of layers with a given layer making use of the services offered by the layer below.
- given layer offers software abstraction, with higher layers unaware of implementation detail
- in Distributed Systems term, it is equal to vertical organization of services into service layers.
Tiered Architecture
- complementary to layering
- tiering is a technique to organize functionality of a given layer and place this functionality into appropriate servers and as a secondary consideration on to physical nodes
- commonly associated with the organization of application and services. (Eg. presentation, business logic, data)
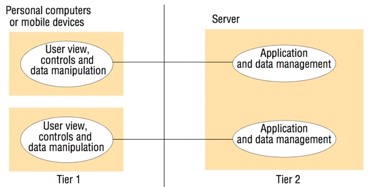
2-tier architecture
- Advantages: Low Latency
- Disadvantages: application logic split across process boundary
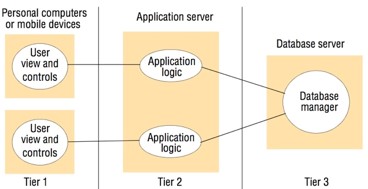
3-tier architecture
- Advantages:
- app logic in one place - good for maintainability
- each tier has well defined roles
- Disadvantages:
- difficulty maintaining 3 servers
- added network traffic and latency in operation
Thin Client
- refers to a software layer that supports window-based UI that is local to the user while executing application programs
- generally for accessing services on a remote computer
- advantages:
- local device can be simpler
- resource-constrained devices can be significantly enhanced with a plethora of networked services and capabilities
- disadvantages:
- network and OS latencies due to the highly interactive graphical nature of thin-client activities can reach unacceptable levels
- Examples: VNC, RealVNC, Remote Desktop, etc
Middleware
- provides a higher-level programming abstraction for developing Distributed Systems through layering
- abstracts over heterogeneity in the underlying infrastructure to promote interoperability and portability
- Limitations:
- not able to support every need in a wide range of applications
- supports a lot of distributed system development for simplifying the programming
Fundamental Model
- takes an abstract perspective to examine individual aspects of a distributed system. There are 3 important aspects:
- Interaction Model - considers structure and sequencing of communication
- Failure Models - considers the ways how a system may fail to operate correctly
- Security Models - how the system is protected against attempts to interfere with proper operation
- purpose of such models are to:
- make explicit all the relevant assumptions about the systems we are modelling
- make generalizations concerning what is possible or not given those assumptions. Generalizations may take the form of general-purpose algorithms or guaranteed desirable properties. Guarantees are dependent on logical analysis, and where appropriate, mathematical proof.
Interaction Model
- Computation occurs within processes
- interactions where processes interact by passing messages resulting in communication and coordination between processes
- model must reflect that communication takes place with delays that are often of considerable duration and that the accuracy of which independent processes can be coordinated is limited by these delays
- Distributed Systems are composed of multiple processes where their behavior and state can be described by a distributed algorithm- a definition of steps to be taken by each of the processes of which the system is composed, including the transmission of messages between them
- processes have its own state consisting of the set of data that it can access and update including the variables in its program
- TWO significant factors affecting interaction processes in a Distributed System
- communication perf is often a limiting characteristic
- impossible to maintain a single global notion of time
There are more but I got real tired and ran out of time so you gotta fill in the blanks yourself
Mid Term Test Questions
-
List and explain FIVE characteristics of Distributed Systems (10 marks)
-
List and discuss the FIVE challenges in developing Distributed Systems (10 marks)
-
You are required to design and Distributed System for GrabCar which is a car hire company. Please sketch out a three-tier solution to the provision of their underlying distributed car hire service. Use this to illustrate the benefits and drawbacks of a three-tier solution considering issues such as performance, scalability, dealing with failure and also maintaining the software over time.
Past Year 2016 Test Questions
Question 1
-
Describe what a Distributed System is. (2 marks)
Answer
-
List and explain THREE benefits obtained with Distributed System. (6 marks)
Answer
-
Provide a Distributed System example that is used in creative and entertainment industries and explain the contribution of that system. (4 marks)
Answer
-
List and describe FIVE characteristics of Distributed Systems. (10 marks)
Answer
-
Explain what client-server computing is and state that which of them is playing the active role or passive role. Explain remote invocation in this context. (6 marks)
Answer
-
A distributed system is described as scalable if it remains effective when there is a significant increase in the number of resources and the number of users. However, these systems sometimes face performance bottlenecks. How can this be avoided? (4 marks)
Answer
-
List and Explain FOUR challenges in achieving Distribution Transparency in Distributed System. (8 marks)
Answer
-
Consider a simple server that carries out client requests without accessing other servers. Explain why it is generally not possible to set a limit on the time taken by such a server to respond to a client request. (2 marks)
Answer
-
Consider there are two communication services have been implemented in asynchronous distributed systems. In service A, a message may be lost, duplicated or delayed and checksums apply only to headers. In service B, messages may be lost, delayed or delivered too fast for a recipient to handle them, but those that are delivered arrive with the correct contents. Describe the classes of failure exhibited by each service. Classify their failures according to their effects on the properties of validity and integrity. Can service B be described as a reliable communication service? (5 marks)
Answer
-
Explain what middleware is and how it is useful in Distributed Systems. (3 marks)
Answer
Question 2
-
A distributed application known as Play and Match for finding lovers had been hacked and millions of user accounts being compromised. Play and Match is a Remote Method Invocation (RMI) application with the client-server architecture. Assuming that you are the security adviser for the application company, please suggest at least FOUR (4) solutions for improving the security of a distributed system. (8 marks)
Answer
-
Describe what is meant by scalability of a system. (2 marks)
Answer
-
List and describe FOUR challenges face in designing scalable Distributed System (8 marks)
Answer
-
Scalability can be achieved by applying different techniques. List these techniques and provide an example. (7 marks)
Answer
Question 3
-
Draw an architecture diagram for the physical and architectural models to describe the design of a Point of Sales (POS) system for Aeon Big supermarket which has over 5000 supermarkets in Malaysia. They have round 25000 computers and generate averagely around 12 million transactions per day. The designed system should be scalable and reliable system due to they going to double up their business in coming year. (15 marks)
Answer
-
Based on the diagram from part a), provide justification for the design and describe the principles you follow to achieve scalability and reliability. (10 marks)
Answer
Question 4
-
Consider using Java Remote Method Invocation for implementing Election service in coming Malaysia election system. Discuss the effect of maybe semantics on the Election service. Explain and provide justification either at-least-once call semantics be acceptable for the Election service or would you recommend at-most-once call semantics. (8 marks)
Answer
-
You are required to use AKKA middleware to build a distributed system for International Auctions.
-
Identify the possible actors and messages that are required in the systems. (5 marks)
Answer
-
Design a communication protocol for bidding an item with a sequence diagram. (8 marks)
Answer
-
-
Contrast Java RMI middleware and AKKA middleware in term of their characteristic. (4 marks)
Answer
Exercises
-
Give five types of hardware resource and five types of data or software resource that can usefully be shared. Give examples of their sharing as it occurs in practice in distributed systems.
Hardware: Hard drives, printers, scanners, server, speakers. Software: files, databases, videos, data objects, music
-
How might the clocks in two computers that are linked by a local network be synchronized without reference to an external time source? What factors limit the accuracy of the procedure you have described? How could the clocks in a large number of computers connected by the Internet be synchronized? Discuss the accuracy of that procedure.
Answer
-
Consider the implementation strategies for massively multiplayer online games as discussed in Section 1.2.2. In particular, what advantages do you see in adopting a single server approach for representing the state of the multiplayer game? What problems can you identify and how might they be resolved?
Answer
-
A user arrives at a railway station that they has never visited before, carrying a PDA that is capable of wireless networking. Suggest how the user could be provided with information about the local services and amenities at that station, without entering the station’s name or attributes. What technical challenges must be overcome?
Answer
-
Compare and contrast cloud computing with more traditional client-server computing? What is novel about cloud computing as a concept?
Answer
-
Use the World Wide Web as an example to illustrate the concept of resource sharing, client and server. What are the advantages and disadvantages of HTML, URLs and HTTP as core technologies for information browsing? Are any of these technologies suitable as a basis for client-server computing in general?
Answer
-
A server program written in one language (for example, C++) provides the implementation of a BLOB object that is intended to be accessed by clients that may be written in a different language (for example, Java). The client and server computers may have different hardware, but all of them are attached to an internet. Describe the problems due to each of the five aspects of heterogeneity that need to be solved to make it possible for a client object to invoke a method on the server object.
Answer
-
An open distributed system allows new resource-sharing services such as the BLOB object in Exercise 1.7 to be added and accessed by a variety of client programs. Discuss in the context of this example, to what extent the needs of openness differ from those of heterogeneity.
Answer
-
Suppose that the operations of the BLOB object are separated into two categories – public operations that are available to all users and protected operations that are available only to certain named users. State all of the problems involved in ensuring that only the named users can use a protected operation. Supposing that access to a protected operation provides information that should not be revealed to all users, what further problems arise?
Answer
-
The INFO service manages a potentially very large set of resources, each of which can be accessed by users throughout the Internet by means of a key (a string name). Discuss an approach to the design of the names of the resources that achieves the minimum loss of performance as the number of resources in the service increases. Suggest how the INFO service can be implemented so as to avoid performance bottlenecks when the number of users becomes very large.
Answer
-
List the three main software components that may fail when a client process invokes a method in a server object, giving an example of a failure in each case. Suggest how the components can be made to tolerate one another’s failures.
Answer
-
A server process maintains a shared information object such as the BLOB object of Exercise 1.7. Give arguments for and against allowing the client requests to be executed concurrently by the server. In the case that they are executed concurrently, give an example of possible ‘interference’ that can occur between the operations of different clients. Suggest how such interference may be prevented.
Answer
-
A service is implemented by several servers. Explain why resources might be transferred between them. Would it be satisfactory for clients to multicast all requests to the group of servers as a way of achieving mobility transparency for clients?
Answer
-
Resources in the World Wide Web and other services are named by URLs. What do the initials URL denote? Give examples of three different sorts of web resources that can be named by URLs. page 26 1.15 Give an example of an HTTP URL. List the main components of an HTTP URL, stating how their boundaries are denoted and illustrating each one from your example. To what extent is an HTTP URL location-transparent?
Answer
-
Give an example of an HTTP URL. List the main components of an HTTP URL, stating how their boundaries are denoted and illustrating each one from your example. To what extent is an HTTP URL location-transparent?
Answer